Cyber Resilience Challenges: Overcoming Cybersecurity Threats
Cyber resilience is crucial for organizations to withstand and recover from cyber threats and incidents. Despite its importance, many face common challenges in achieving an optimal level of cyber resilience. Understanding these challenges and adopting strategic measures to overcome them is essential for maintaining security, continuity, and integrity in the digital realm.
New initiatives such as the EU DORA, the US Sound Practices to Strengthen Operational Resilience (OCC, Federal Reserve, FDIC), and the UK FCA/PRA Operational Resilience Regulation are changing the business landscape. Enterprise Architecture (EA) and Security, Risk, and Compliance (GRC) teams face various operational resilience challenges posed by upcoming financial sector regulations.
Understanding Cyber Resilience
Cyber resilience enables organizations to withstand cyber threats, maintaining operations through detection, response, and attack recovery.
At the recent MEGA EA Exchange 2023 digital conference, founder and CEO Trustable Olivier Patole spoke with Paul Estrach, Product Marketing Director at MEGA International, and Cyril Amblard-Ladurantie, Senior Product Marketing Manager at MEGA International. The three experts discussed how to foster active collaboration among EA and GRC teams.
In terms of cyber resilience, IT is the initial stage, involving various individuals. This includes the Chief Information Security Officer (CISO) and their security team, the IT department, and Enterprise Architecture (EA) personnel, each assigned different responsibilities.
The CISO oversees cyber security management and incident detection, ensuring prompt organization-wide alerts. The IT team concentrates on maintaining critical asset inventories within the information system. The architecture team serves as the link between critical assets and applications. Subsequently, the business process becomes the next crucial phase.
Responsibilities for cyber resilience extend to the top of organizations, with boards potentially facing legal accountability for non-compliance. Boards seek assurance on asset protection and business continuity amidst incidents. Risk and compliance teams manage risks, implementing necessary controls and procedures. Cyber resilience intersects IT, business, and compliance realms, necessitating effective team communication.
Despite organizational-wide involvement in cyber resilience, inadequate inter-team communication poses a significant challenge.
READ: What is DORA?
The Need for a Connected Approach to Cyber Resilience
To properly address the individual challenges, we must focus on the qualitative challenge. We need to lean on different people within the organization. Each individual needs others from different departments to perform personal tasks.
If we take for instance the case of a failure of a third party, we need to involve procurement, as procurement is in charge of the third-party registry. The procurement department needs to open discussions with IT as the IT department maintains the critical asset inventory. Discussion with business stakeholders must occur to identify the key activities at the top of this application. Different dots within an organization must be connected to address cyber resilience challenges.
There is a real need to establish a continuous trend. If there is a failure in the third-party register, the organization must be able to understand where the third party plays into its processes. Does it impact a critical process or just a secondary process? What is the impact on the whole trend? Will it impact customers? Will it impact the financial market as a whole?
At the business level and also in IT, people don't have the required vision. They can't tell you what process is powered by the applications and technology and what happens if one fails. Are there proper business continuity plans (BCPs), continuity, and disaster recovery plans in place? Can the get organization back into a business model? This is another major challenge regarding cyber resilience.
It's crucial to identify the criticality of the third party. However, it can be quite difficult to identify high-risk parties. It’s easier to identify which third parties are linked with an application, asset, or process.
In this way, we can identify if there is a net stance process outside the company. We can see if there is support from the third party. We can identify the key third party we need to assess.
“Everybody is involved in cyber resilience, and everyone needs each other to achieve their objectives. Everyone needs to speak the same language. That's probably the biggest challenge. Talking the same language and having the same taxonomy. That's probably where the main challenge lies.”
Cyber Resilience as a Comprehensive Transformation Project
Cyber resilience is a major transformation for an organization. It involves the entire organization: the board, the CISO, the Chief Information Office (CIO), risk and compliance, and procurement teams. The legal team will be involved as clauses regarding third parties will need to be drafted onto contracts to ensure compliance. IT processes will be impacted as will business continuity processes. Compliance processes and third-party management processes will also be impacted.
It's also a technological challenge because all these processes are supported by different applications. For example, the IT registry, a GRC tool, a business continuity tool, or a third-party management tool. All of these applications will be impacted by cyber resilience regulations.
“I think what we're trying to say is that it's not just a trivial matter - it's going be massive. It will be on the scale of the GDPR.”
Four Steps to Ensure Cyber Resilience
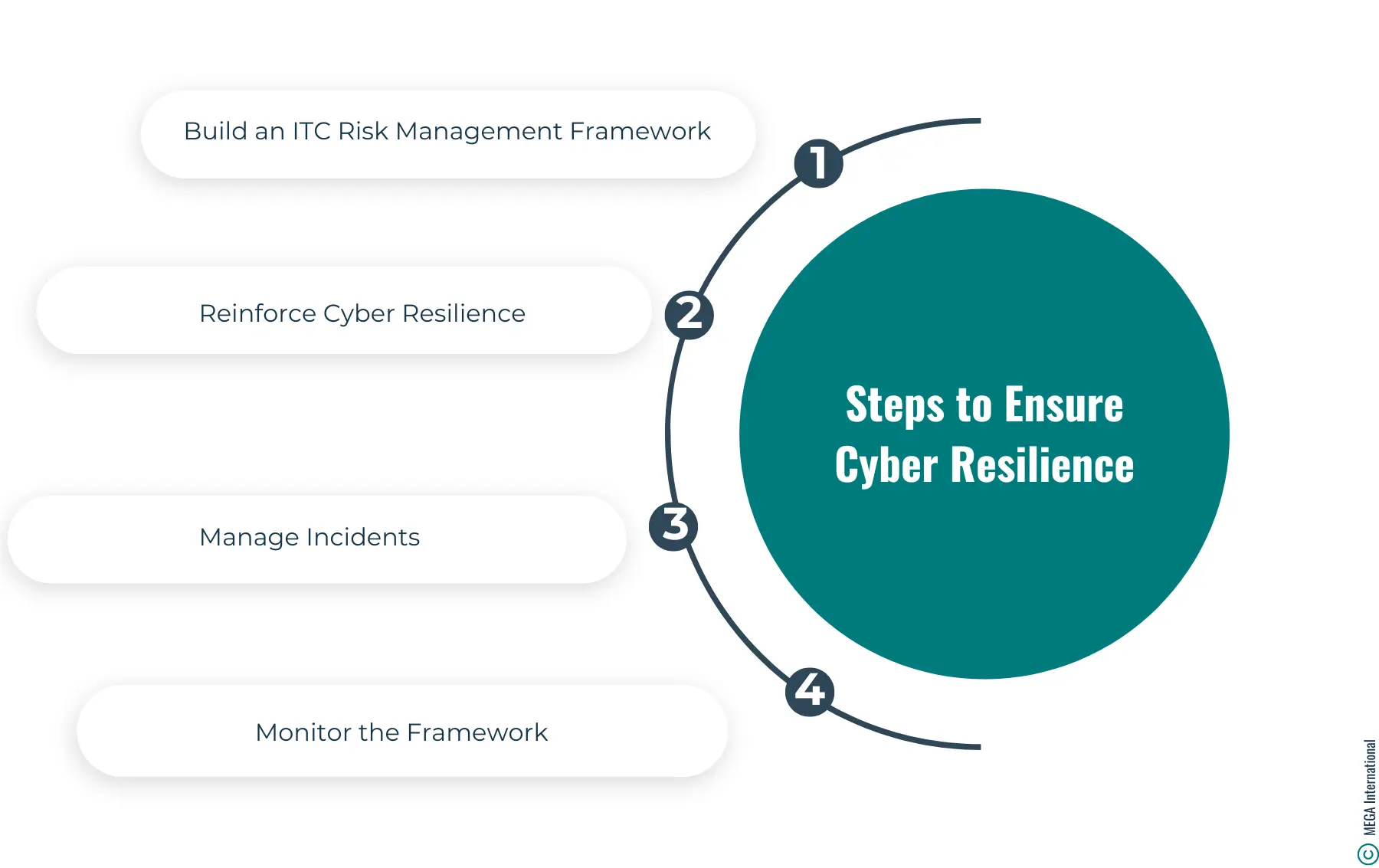
Step 1: Build an ITC Risk Management Framework
The required approach to successfully executing a major transformation project that impacts a process is to look internally. An organization probably already has systems in place to create a risk management framework.
It is crucial to connect the application and the process. If an incident impacts an application, they can quickly identify whether it will affect the whole business, if it's a minor incident, or if it will disrupt the entire market. The risks attached to the first parties must be identified.
Today, companies are connected to an ecosystem and rely on third parties for different activities. We analyze different processes within an organization. One aspect may be internal, and the second will be external. Building an internal and external ITC risk management framework is the first step.
Step 2: Reinforce Cyber Resilience
It's essential to identify and analyze third parties' natural cyber resilience. This will ensure a global view and a good awareness of the level of resilience. Organizations can then build resilience and reinforce their capabilities and services. Reinforcing other services is the next step.
Step 3: Manage Incidents
A company usually has BCP and public relations (PR) plans. These must be tested to ensure that the organization can resume business as usual quickly in case of disruption.
When incidents occur, a complete root cause analysis must be performed to enable remediation, and incidents must be declared to regulatory authorities. The incident management must be exemplary to ensure compliance with different cyber resilience regulations. Ensuring excellent incident management strategies is the third step.
Step 4: Monitor the Framework
Assessing an internal application is elementary, but evaluating a third-party application can be complex. Companies must be able to consider third parties regarding cyber resilience consistently.
To do this, an organization must understand how the third party manages security. The processes in place must be understood. If a mechanism is deployed within the infrastructure and IT assets, its efficiency must be understood. Monitoring the framework is, therefore, the fourth step.
Different activities must be performed to assess a third-party application. These include penetration testing to evaluate the mechanism's efficiency. The IT architecture must be analyzed. Document reviews must analyze business processes. Interviews should be held with key people within the organization.
This provides a global view of the cybersecurity maturity of the third parties. This allows professionals to provide clients with a rating of a third party, such as AAA or D minus, and so on. Essentially, it is a continuous audit of the third parties.
Cybersecurity threats, information systems, and assets evolve continuously. These variables must all be considered to perform a relevant evaluation of third-party applications.
It is both an internal and external challenge that requires a global view. This is the keystone for cyber resilience.
Managing the complexity of cyber resilience is difficult, but many companies already have internal solutions. They already have a common taxonomy and language. They have a common registry where they manage processes, applications, technology, and risk. There is usually an established GRC model to manage risks and controls related to IT. In partnership with other entities, companies can develop BCPs to manage the cyber risk of third parties.
Ultimately, cyber resilience is everyone's business within an organization. Collaboration must be fostered across all stakeholders to strengthen an organization’s cyber resilience.
But why is cyber resilience important in cybersecurity?
Cyber resilience is crucial in cybersecurity as it enhances an organization's ability to mitigate risks and handle cyber threats effectively. By being cyber-resilient, organizations can minimize the impact of attacks, maintain business continuity, and protect sensitive data from unauthorized access.
Related: Will AI replace cybersecurity experts?
Common Challenges in Achieving Cyber Resilience
Achieving cyber resilience is not without its challenges. Let's explore some of the most common obstacles to bolstering cyber defenses. Organizations can better prepare themselves against evolving cyber threats by understanding and addressing these challenges.
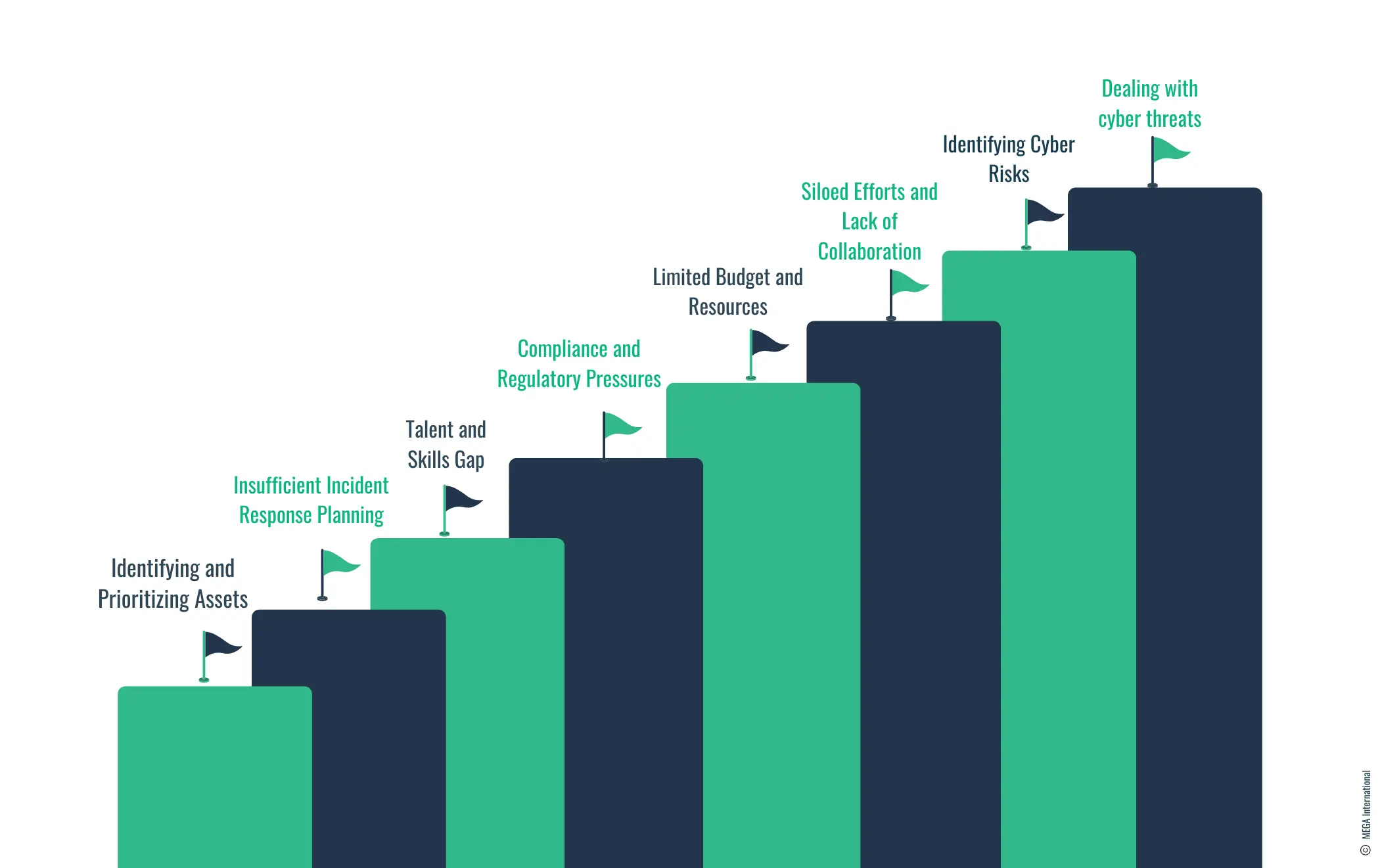
Identifying and Prioritizing Assets
Challenge: Many organizations struggle with identifying which assets are most critical to their operations and require protection.
Solution: Conduct thorough asset identification and classification exercises to prioritize assets based on their criticality and value to the organization. Implement a tiered security approach that allocates more resources and protective measures to higher-priority assets.
Insufficient Incident Response Planning
Challenge: Organizations often lack a comprehensive incident response plan, leaving them unprepared to efficiently manage and recover from cyber incidents.
Solution: Develop and regularly update an incident response plan with clear procedures for various incidents. Conduct regular drills and simulations to test and refine the plan, ensuring all stakeholders know their roles and responsibilities.
Talent and Skills Gap
Challenge: A widespread talent and skills gap in cybersecurity makes it difficult for organizations to find and retain qualified personnel.
Solution: Invest in training and development programs to upskill existing staff. Consider outsourcing certain cybersecurity functions to specialized firms or adopting automated security solutions to alleviate the pressure on in-house teams.
Compliance and Regulatory Pressures
Challenge: Navigating the complex landscape of cybersecurity regulations and compliance requirements can be overwhelming and costly.
Solution: Develop a compliance framework that aligns with industry standards and regulatory requirements. Consider leveraging compliance management software to streamline and automate compliance processes.
Limited Budget and Resources
Challenge: Cybersecurity initiatives often compete with other business priorities for limited budgets and resources.
Solution: Advocate for cybersecurity as a critical business enabler and risk management tool. Prioritize spending on measures that offer the most significant risk reduction and leverage cost-effective solutions like open-source tools and cloud-based services.
Siloed Efforts and Lack of Collaboration
Challenge: Cyber resilience efforts are often fragmented across different departments, leading to inefficiencies and gaps in security.
Solution: Foster a culture of collaboration and shared responsibility for cybersecurity across all levels of the organization. Establish cross-functional teams to coordinate cybersecurity initiatives and ensure a unified approach to cyber resilience.
Identifying Cyber Risks
Challenge: Identifying and accurately assessing cyber risks can be difficult due to the complexity of IT environments and the sophistication of potential threats.
Solution: Implement a continuous risk assessment process that leverages automated tools and expert analysis to identify potential vulnerabilities and threats. This process should include regular vulnerability scans, penetration testing, and the use of threat intelligence to understand emerging risks. Engaging in cybersecurity frameworks, such as those provided by NIST, can offer structured approaches to identifying, assessing, and managing cyber risks. Additionally, fostering a culture of security awareness among employees can help identify phishing attempts and other social engineering tactics that automated systems might not catch.
Dealing with cyber threats
Challenge: Effectively dealing with cyber threats involves detecting them and responding swiftly and efficiently to mitigate damage. The dynamic nature of cyber threats means that organizations must be prepared to counteract known threats and adapt to novel and evolving tactics.
Solution: To address this challenge, organizations should employ a multi-layered defense strategy that includes preventive measures and responsive actions.
This involves:
- Preventive Measures: Implement strong security policies, conduct regular security training for employees, use up-to-date antivirus software, employ firewalls, and ensure systems are regularly patched and updated to protect against known vulnerabilities.
- Detection and Response: Leveraging advanced security technologies such as intrusion detection systems (IDS) and security information and event management (SIEM) systems for real-time monitoring and alerting of potential threats. Additionally, having an incident response team equipped with a well-defined incident response plan ensures the organization can respond to and recover from incidents as quickly as possible.
- Threat Intelligence: Utilizing threat intelligence platforms to stay informed about the latest cyber threats and leveraging this information to enhance detection capabilities and refine defensive measures.
- Regular Testing: Conduct penetration testing and red team exercises to simulate attacks and identify vulnerabilities in the organization's defenses before actual attackers can exploit them.
Managing disruptions effectively
Challenge: Cyber incidents can disrupt business operations, affecting services, customer trust, and overall reputation. Managing these disruptions effectively requires a proactive approach to minimize impact and restore operations quickly.
Solution: Effective disruption management involves several vital strategies
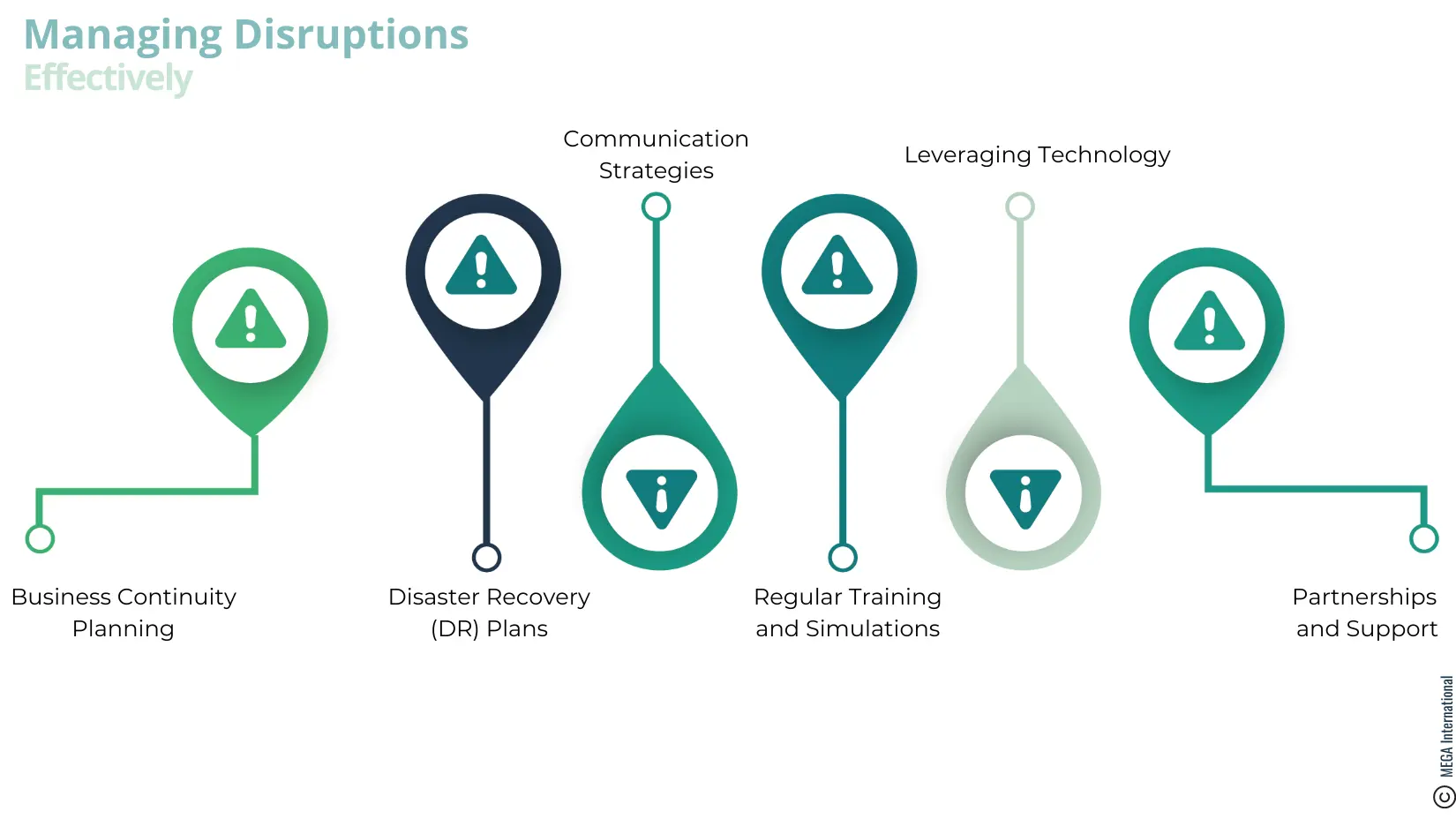
- Business Continuity Planning (BCP): Develop comprehensive business continuity plans that outline how operations can continue in the event of various types of cyber incidents. These plans should include details on maintaining critical services, data backup and recovery procedures, and alternative communication channels.
- Disaster Recovery (DR) Plans: Alongside BCP, have detailed disaster recovery plans focused explicitly on restoring IT systems and data access after a cybersecurity incident. DR plans should be regularly tested to ensure they can be executed effectively in an emergency.
- Communication Strategies: Prepare clear communication strategies for internal and external stakeholders, including employees, customers, and partners. Transparent and timely communication during a disruption can help manage expectations and mitigate damage to trust and reputation.
- Regular Training and Simulations: Conduct regular training sessions and simulation exercises for relevant staff to ensure they are familiar with the BCP and DR plans and understand their roles in managing disruptions. This training should include simulations of cyber incidents to test and refine the effectiveness of plans and response actions.
- Leveraging Technology: Implement technologies that can help mitigate the impact of disruptions, such as cloud-based services for data redundancy, automated backups, and systems that can detect and isolate cybersecurity incidents to prevent their spread.
- Partnerships and Support: Establish relationships with external cybersecurity experts, law enforcement, and industry groups. These partnerships can provide additional support and resources during and after a cyber incident, aiding in quicker recovery.
Third-Party Risk Management
Challenge: Organizations must ensure their third parties adhere to the same cybersecurity standards and practices as they do internally. The complexity increases with the number of third-party relationships, each potentially exposing the organization to different levels of risk.
Solutions: Various practices and strategies can be developed to manage cybersecurity risks associated with third-party relationships effectively:
- Conduct Thorough Due Diligence: Conduct comprehensive due diligence before engaging with any third party to assess their cybersecurity posture. This includes evaluating their security policies, incident response capabilities, and compliance with relevant regulations and standards.
- Establish Clear Contracts and SLAs: Define clear cybersecurity expectations, responsibilities, and requirements in contracts and service level agreements (SLAs) with third parties. Include requirements for regular security assessments and audits to ensure compliance.
- Implement Continuous Monitoring: Adopt a continuous monitoring approach to oversee third-party security practices. Use tools and services that provide real-time insights into third-party security postures and potential breaches that could impact your organization.
- Develop a Third-Party Risk Management Program: Establish a formal third-party risk management program that outlines processes for identifying, assessing, monitoring, and mitigating risks associated with external entities. This program should be integrated into the organization's overall cyber resilience strategy.
- Ensure Incident Response Coordination: Include third parties in your incident response planning. Ensure clear protocols for communication and coordination in the event of a security incident involving a third-party service or product.
- Educate and Train Third Parties: Where possible, provide cybersecurity training and resources to third parties, mainly if they handle sensitive data or access critical systems. Helping them improve their security practices benefits both parties.
- Regularly Review and Update Third-Party Relationships: Review third-party vendors' security performance and compliance. Update risk assessments and strategies based on third-party services, products, or security posture changes.
IT, Business, and Compliance challenges and solutions in cybersecurity
IT Challenges and Solutions
Challenge: Rapidly Evolving Cyber Threats
Solution: Adopt proactive cyber defense strategies, including continuous threat intelligence gathering, advanced threat detection systems, and regular security assessments to identify and mitigate vulnerabilities.
Challenge: Integration of Security into IT Operations
Solution: Implement a security-by-design approach, ensuring that security considerations are integrated at every stage of IT project development and execution. Utilize automation and orchestration tools to streamline security operations.
Business Challenges and Solutions
Challenge: Aligning Cyber Resilience with Business Objectives
Solution: Establish a cross-functional cyber resilience team with business leaders to ensure cybersecurity strategies are supported and aligned with business objectives. Regularly review and update the cyber resilience plan to reflect changes in business strategy.
Challenge: Ensuring Business Continuity Amidst Cyber Threats
Solution: Develop and regularly test business continuity and disaster recovery plans that address cyber incidents. This includes identifying critical business functions and establishing protocols for rapid restoration during a cyberattack.
Compliance Challenges and Solutions
Challenge: Navigating a Complex Regulatory Landscape
Solution: Maintain an up-to-date understanding of relevant regulations and standards and implement a compliance management system that can dynamically adjust to changes in the regulatory environment. Regular training and awareness programs for staff on compliance matters are essential.
Challenge: Ensuring Data Privacy and Security
Solution: Adopt a comprehensive data protection strategy that includes encryption, access control, and data lifecycle management. Regular audits and assessments should be conducted to ensure compliance with data protection regulations like GDPR and CCPA.
Integrated Strategies for Enhanced Cyber Resilience
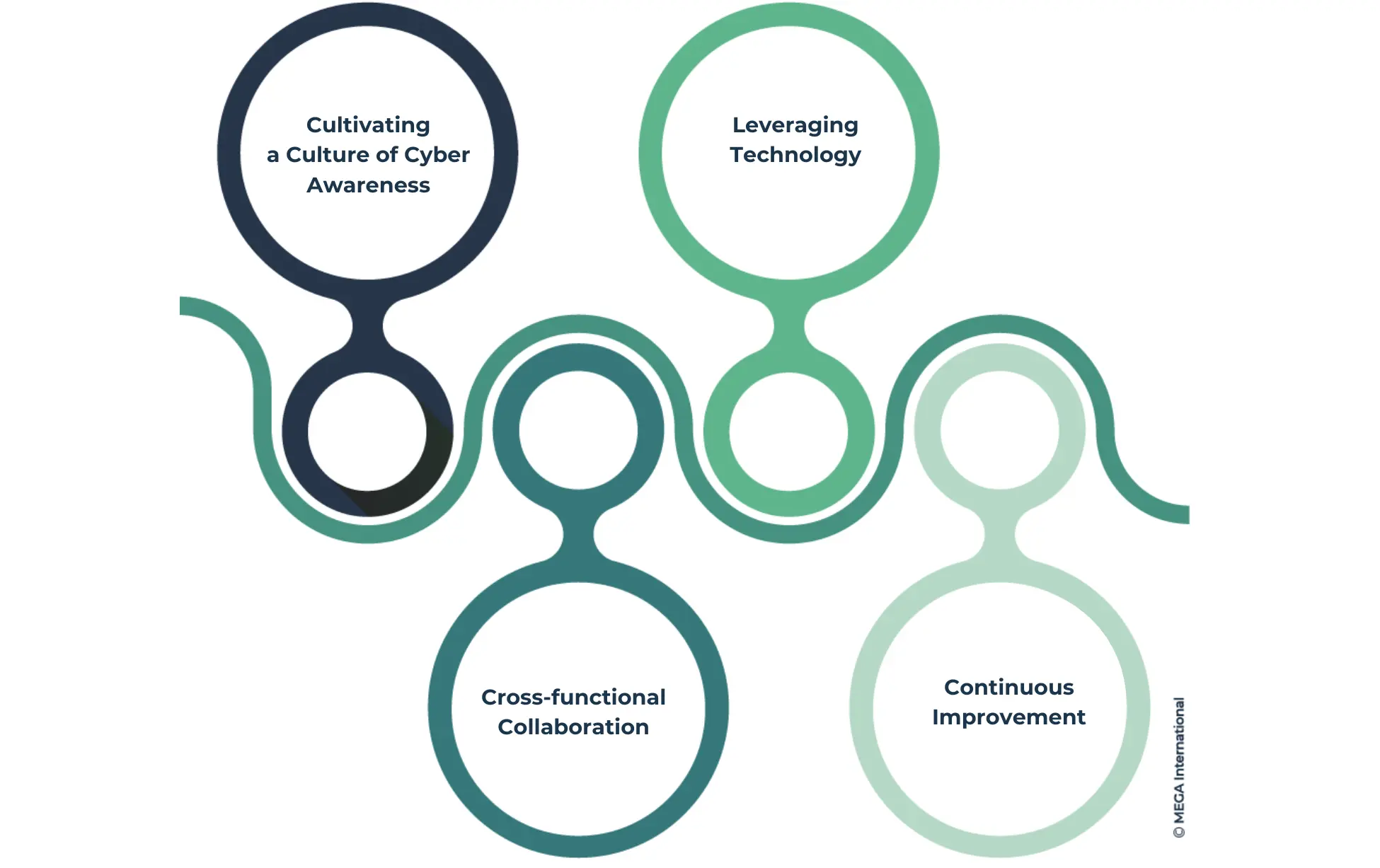
- Cultivating a Culture of Cyber Awareness: Foster a culture of cyber resilience across the organization through regular training programs, simulations, and awareness campaigns to ensure that all employees understand their role in maintaining cybersecurity.
- Leveraging Technology: Utilize advanced cybersecurity technologies, including AI and machine learning, for predictive threat analysis, anomaly detection, and automated response mechanisms. This technological leverage is crucial for staying ahead of cyber adversaries.
- Cross-functional Collaboration: Encourage ongoing collaboration between IT, business, and compliance teams to ensure a unified approach to cyber resilience. This can be facilitated through regular meetings, shared objectives, and integrated planning exercises.
- Continuous Improvement: Adopt a continuous improvement mindset for cyber resilience strategies, regularly reviewing and updating policies, procedures, and technologies in response to new threats and business changes.
The Need for a Connected Approach to Cyber Resilience
Addressing cyber resilience challenges demands a collaborative approach within an organization, emphasizing the need for cross-departmental coordination. For instance, handling a third-party failure requires the procurement team to liaise with IT for an updated critical asset inventory and engage with business stakeholders to evaluate the impact on essential operations. This scenario underscores the necessity of connecting various organizational segments to forge a comprehensive resilience strategy.
A proactive stance is essential in understanding the role and criticality of third parties within organizational processes and assessing their impact on operations, customer relations, and potentially the broader financial market. Many organizations face hurdles in achieving a clear overview of how applications and technologies underpin their processes and the implications of their failure, highlighting the importance of robust business continuity and disaster recovery plans.
The challenge extends to recognizing high-risk third parties, necessitating a detailed understanding of their linkage to organizational applications, assets, or processes. This identification is crucial for evaluating external dependencies and ensuring appropriate support mechanisms are in place.
The essence of overcoming these challenges lies in fostering a culture of communication where everyone within the organization speaks a unified language of cyber resilience, underscoring the collective responsibility of safeguarding against cyber threats.
Summary
The crucial significance of cyber resilience for organizations is brought into focus amidst evolving regulations and intricate interconnections. Effective collaboration, communication, and a holistic approach are emphasized to navigate challenges successfully. Prioritizing robust risk management frameworks, resilience reinforcement, incident management, and continuous monitoring are highlighted as essential steps. Ultimately, cyber resilience is underscored as a shared responsibility across all stakeholders within an organization.
FAQs
Some critical cyber resilience challenges include data breaches, malware attacks, and evolving cyber threats. Organizations should implement effective cyber resilience strategies to overcome these challenges, invest in cybersecurity awareness and training, and continuously assess and improve security measures.
A cyber resilience strategy is essential for organizations to ensure business continuity, protect critical data and assets, maintain customer trust, and effectively mitigate the impact of cyber attacks.
Governance, Risk and Compliance Related Content
Enhance operational resilience using integrated risk management
MEGA HOPEX for GRC
Request a demonstration of HOPEX for GRC, and see how you can have immediate value of your projects.